AUDIO NETWORK SECURITY: INTRODUCING DANTE DOMAIN MANAGER
Audio networking has brought many improvements to the world of professional audio: virtually limitless channel counts, minimal and easy cabling, simple redundancy - just to name a few. It has also brought us new functionality that didn’t exist before, such as the separation of functional and physical connections (the network as a patch panel), storing and recalling patches in memory, monitoring the status of individual inputs / outputs and sharing the same infrastructure for other functionality, such as user interfaces, lighting and video.
Another useful new feature of audio networks is the possibility to connect to a system through any network port to have instant access to everything, from routing to word clock selection. Audinate has developed this functionality to the limit, making use of Apple’s ‘Bonjour’ service. Dante Controller, Audinate’s control software, automatically discovers all Dante devices on the network and even supports multiple users accessing the system simultaneously.
Of course, exciting functions also introduces new issues - in this case security. In the ‘old times’ a person could sabotage a system - by accident or on purpose - by pulling out a few cables locally, affecting a few connections at most, leaving the rest of the system operational. In a networked audio system, however, a user can connect to the system and then have access to every single connection, potentially affecting the whole system.
For small systems, physical measures such as blocking access to ports by mechanical means, and careful instructions to users, can help to prevent accidents from happening. If a Wireless Access Point (WAP) is included in the system, 'Wi-Fi Protected Access' (WPA) security can be used to restrict access. Also MAC filtering can be used to restrict access. However, in all cases - no matter what measures are applied to prevent unauthorized access - the bottleneck is the user; authorised or not, accidentally or intentional.
Recently, Audinate developed a full scope solution for the issue. In this case, ‘full scope’ doesn’t mean a small tool to manage system access a little more, but a fully-fledged software solution that deals with the issue for once and for all. It’s called Dante Domain Manager (DDM) and it completely secures and manages access to the Dante part of the network.
To implement DDM, a ‘DDM server’ can be added to the network - either a physical computer (a laptop or desktop PC) or a virtual one (running on an existing server in the network). This server has the DDM server application and license installed. It’s possible to add a second server as a back-up in case the first one fails.
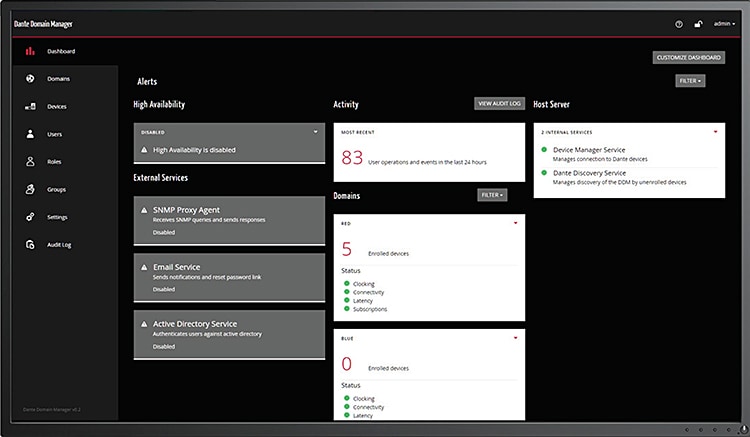
Initially, all Dante devices are in an open ‘unmanaged’ domain, accessible by anyone who connects to the network with Dante Controller. The DDM server administrator can now ‘enrol’ Dante devices to become part of a ‘domain’ - which is just a way of listing devices in separate groups. These domains can be created to represent areas (e.g. ‘stadium’, ‘conference room’, ‘lobby’ etc), functionality (e.g. ‘PA system’, ‘paging’, ‘evacuation’)… or any other classification. Once a device is part of a domain, it can no longer be seen in an unauthorised version of Dante Domain Manager.
Next, the DDM server administrator can enrol ‘users’ and assign roles (i.e. which functionality a user can access) and domains to each user. This way the whole network can be managed - Dante Controller users only see and have access to the devices and functions they are authorised for by the system administrator. A user can see his or her assigned domains only after logging in to the server with a user name and password. Also, additional information and monitoring is available through a simple ‘dashboard’ web interface that can be accessed through a web browser such as Chrome or Safari.
Corporate IT managers and administrators will also appreciate DDM, as it supports the Simple Network Management Protocol (SNMP), answering to enquiries from other programs connected to the network, as well as the IT-world standard Lightweight Directory Access Protocol (LADP) and Windows Active Directory protocol, allowing DDM to use the IT system’s managed user-profile databases to check authorisation of users. Finally, DDM makes it possible to mix network domains, which makes management of large scale systems easier, and allows even audio to cross over to different network domains.
Is DDM for everyone? For small systems with a limited number of users and restricted network access - for example in smaller live systems, where there’s only a few switches - then DDM might be a bit too much. It’s possible to install DDM of course, but a license comes at a cost. For a large scale system, however, where the network is exposed to a large group of users, DDM could be considered a must.